Security Bulletin
2020-11-30
- A critical vulnerability has been fixed in the packed SQL+JQL Driver.
Please upgrade to the 3.6.5 version or above version to resolve this issue
2020-09-04
- We have contracted the services of some ethical hackers in Rusia to find vulnerabilities of the app. As a result of this research, some vulnerabilities have been detected affecting to some URLs susceptible of XSRF attacks if a Jira Administrator with an active Jira session opened in the same browser visits a malicious site which potentially could manage all the BIRT reports (edit, delete, change access permissions and available locations) as well as upload new ones. This last action is considered as a high-risk vulnerability.
Please upgrade to the 3.6.4 version or above version to resolve this issue
2020-07-01
A security threat was detected in 3.6.2 and previous versions allowing a malicious Jira user to perform an XSS attack (Javascript injection). Credits for Ivan Rumak and Alexey Rumak that reported it via https://detectify.com/. Thank you!
Please upgrade to the 3.6.3 version or above version to resolve this issue
2018-03-23
What is the origin of the threat?
Eclipse BIRT reports as much powerful as plugins. They can run Java code on the Server via scripting. This is a very powerful feature but it must be restricted to trusted users and groups who can upload reports into the System.
Unfortunately, version between 2.0.0 and 2.2.0 does not restrict this feature to trusted users only.
How might it affect my Jira instance?
A potential attacker can run Java code on Jira with no limits. It is possible to access to the full Jira API (create users, change permissions, etc) and Java in general: download/upload files, execute programs with the same security that the OS user running Jira server.
Is it safe to run an Eclipse BIRT report?
Absolutely. This affects to the Eclipse BIRT report sources only. Just like any other Server technology: JSP, PHP, etc. BIRT reports are XML files that are interpreted in the server returning HTML code to the users' browser.
How serious is this thread?
It has the highest risk level possible: Critical.
What are the versions affected?
Unfortunately, all the apps between the 2.0.0 and 2.2.0 versions of the Eclipse BIRT for Jira app is affected by this vulnerability: any logged in Jira user with Browse Project permission can upload Eclipse BIRT reports into Jira. Jira Public instances allowing anyone to create an account, are at the highest risk possible.
How can it be fixed?
Upgrade to the 2.3.0 version as soon as possible.
Upgrading it is a breeze: it requires one click only and everything will go safe.
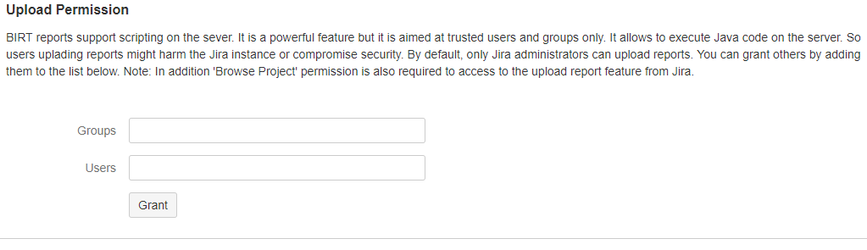
The newer version restricts uploading Eclipse BIRT reports to Jira administrators only. Jira administrators are able to delegate this feature to other Jira users and groups that they trust on. Please see the new form to configure upload permissions available from the 2.3.0 version:
Eclipse BIRT reports are stored in the file system in the directory:
${JIRA_HOME}/kintosoft/birt-viewer/reports
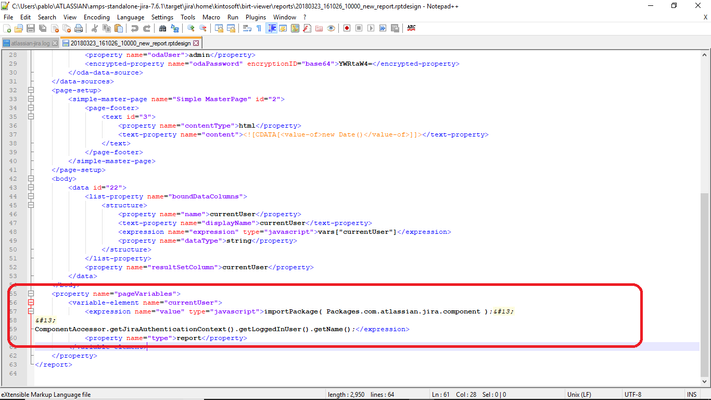
Eclipse BIRT reports are XML files, therefore they can be easily edited: Please, search for any Java code inside and review that everything is fine.
Example:
Depending on who can log in to Jira the risk might be higher. In organizations where only trusted users (employees, etc) can log in Jira the risk might be considered less severe. However, Public Jira instances are at the highest risk. It would be possible for an attacker to run an Eclipse BIRT report opening a backdoor, and delete the report later. So:
- Upgrade to the 2.3.0 version of the app to avoid everyone (unless Jira administrators to upload Eclipse BIRT reports into Jira).
- Check that the Eclipse BIRT reports stored in your Jira instance are healthy. The XML files are stored in the ${JIRA_HOME}/kintosoft/birt-viewer/reports/ directory.
- Re-start Jira to kill any potential unsafe Java code running.
- Check the health of your OS
Has anyone reported any attack?
No. The development team detected the risk, created a fix, notified it to Atlassian, and published this public security threat alert.
I have more questions or concerns...
Please do not hesitate to contact us at atlassian@marketplace.expert. We will try to answer any questions ASAP.